©2021 Reporters Post24. All Rights Reserved.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning about hackers actively exploiting a critical vulnerability in Adobe ColdFusion ioutlet la milanesa and camicie benetton outlet benetton outlet shop online www geox it saldi geoxoutlet.shop zaini gabs outlet and camicie outlet benetton outlet donna outlet gabs borse geox.it outlet outlet benetton online outlet geox spaccio zaini gabs outlet harmont and blain dentified as CVE-2023-26360 to gain initial access to government servers.
The security issue allows executing arbitrary code on servers running Adobe ColdFusion 2018 Update 15 and older, and 2021 Update 5 and earlier. It was exploited as a zero day before Adobe fixed it in mid-March by releasing ColdFusion 2018 Update 16 and 2021 Update 6.
At the time, CISA published a notice about threat actors exploiting the flaw and urged federal organizations and state services to apply the available security updates.
In an alert today, America’s Cybersecurity Defense Agency warns that CVE-2023-26360 is still leveraged in attacks, showcasing incidents from June that impacted two federal agency systems.
“In both incidents, Microsoft Defender for Endpoint (MDE) alerted of the potential exploitation of an Adobe ColdFusion vulnerability on public-facing web servers in the agency’s pre-production environment” – CISA
The agency notes that “both servers were running outdated versions of software which are vulnerable to various CVEs.”
CISA says that the threat actors leveraged the vulnerability to drop malware using HTTP POST commands to the directory path associated with ColdFusion.
The first incident was recorded on June 26 and relied on the critical vulnerability to breach a server running Adobe ColdFusion v2016.0.0.3.
The attackers conducted process enumeration along with network checks and installed a web shell (config.jsp) that allowed them to insert code into a ColdFusion configuration file and extract credentials.
Their activities included deleting files used in the attack to hide their presence and creating files in the C:\IBM directory to facilitate malicious operations undetected.
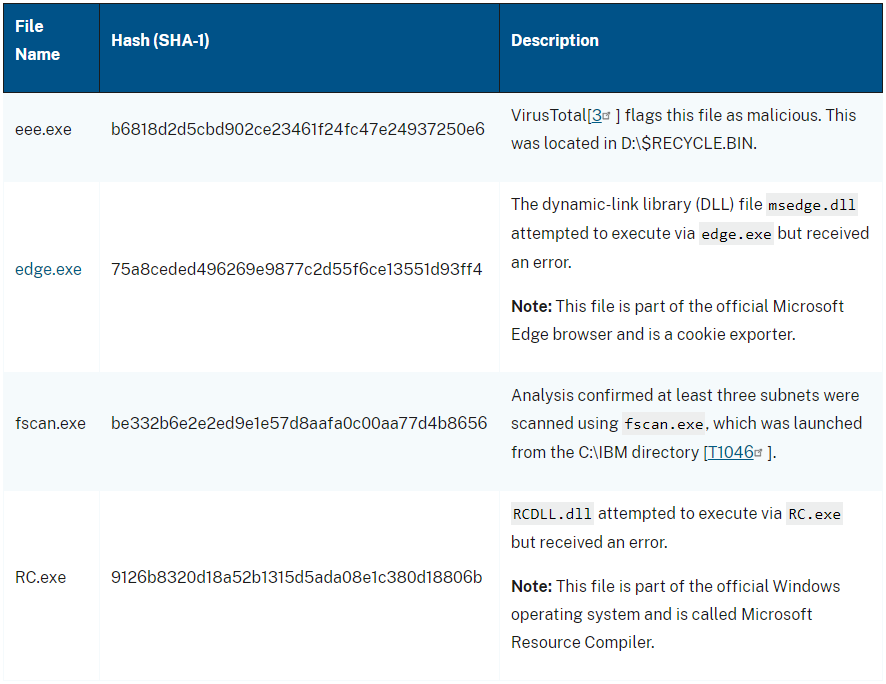
The second incident occurred on June 2 when the hackers exploited CVE-2023-26360 on a server running Adobe ColdFusion v2021.0.0.2.
In this case, the attackers gathered user account information before dropping a text file that decoded as a remote access trojan (d.jsp).
Next, they attempted to exfiltrate Registry files and security account manager (SAM) information. The attackers abused available security tools to access SYSVOL, a special directory present on every domain controller in a domain.
In both cases, the attacks were detected and blocked before the intruders were able to exfiltrate data or move laterally, and the compromised assets were removed from crucial networks within 24 hours.
CISA’s analysis categorizes the attacks as reconnaissance efforts. However, it is unknown if the same threat actor is behind both intrusions.
To mitigate the risk, CISA recommends upgrading ColdFusion to the latest available version, applying Cybersecurity network segmentation, setting up a firewall or WAF, and enforcing signed software execution policies.


