©2021 Reporters Post24. All Rights Reserved.
Hackers are deploying a new malware named ‘Frebniss’ on Microsoft’s Internet Information Services (IIS) that stealthily executes commands sent via web requests.
Frebniis was discovered by Symantec’s Threat Hunter Team, who reported that an unknown threat actor is currently using it against Taiwan-based targets.
Microsoft IIS is a web server software that acts as a web server and a web app hosting platform for services like Outlook on the Web for Microsoft Exchange.
In the attacks seen by Symantec, the hackers abuse an IIS feature called ‘Failed Request Event Buffering’ (FREB), responsible for collecting request metadata (IP address, HTTP headers, cookies). Its purpose is to help server admins troubleshoot unexpected HTTP status codes or request processing problems.
The malware injects malicious code into a specific function of a DLL file that controls FREB (“iisfreb.dll”) to enable the attacker to intercept and monitor all HTTP POST requests sent to the ISS server. When the malware detects specific HTTP requests the attacker sends, it parses the request to determine what commands to execute on the server.
Symantec says that the threat actors first need to breach an IIS server to compromise the FREB module, but they could not determine the method used to gain access initially.
The injected code is a .NET backdoor that supports proxying and C# code execution without ever touching the disk, making it completely stealthy. It looks for requests made to the logon.aspx or default.aspx pages with a specific password parameter.
A second HTTP parameter, which is a base64 encoded string, instructs Frebniis to communicate and execute commands on other systems via the compromised IIS, potentially reaching protected internal systems that are not exposed to the internet.
The malware supports the following commands:
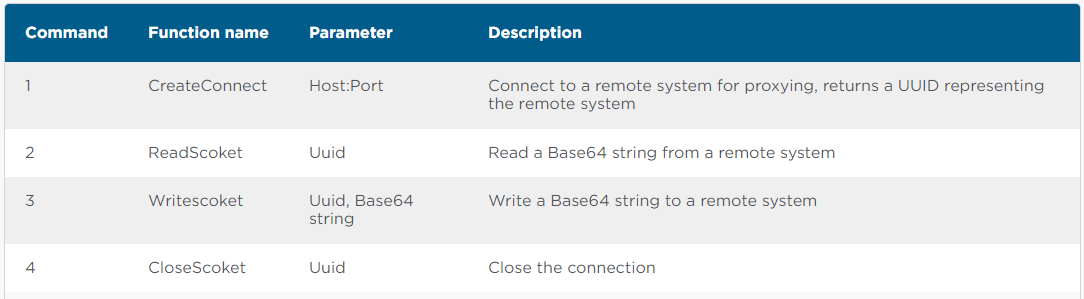
“If an HTTP call to logon.aspx or default.aspx is received without the password parameter, but with the Base64 string, the Base64 string is assumed to be C# code that will be executed straight in memory,” explains Symantec’s report.
“The Base64 string is decoded and then decrypted (xor 0x08) and is expected to be an XML document with the C# code to be executed in the ‘/doc’ node under the ‘data’ attribute (E.g. <doc data=C# code>).”
The main advantage of abusing the FREB component for the described purposes is evading detection from security tools. This unique HTTP backdoor leaves no traces or files and creates no suspicious processes on the system.
Although the initial compromise pathway is unknown, updating your software is generally recommended to minimize the chances of hackers exploiting known vulnerabilities.
Advanced network traffic monitoring tools might also help detect unusual activity from malware like Frebniis.
In October 2022, Symantec discovered another malware used by the Cranefly hacking group that abused ISS logs to send and receive commands from the C2 server without raising any alarms.


