©2021 Reporters Post24. All Rights Reserved.
Users looking to activate Windows without using a digital license or a product key are being targeted by tainted installers to deploy malware designed to plunder credentials and other information in cryptocurrency wallets.
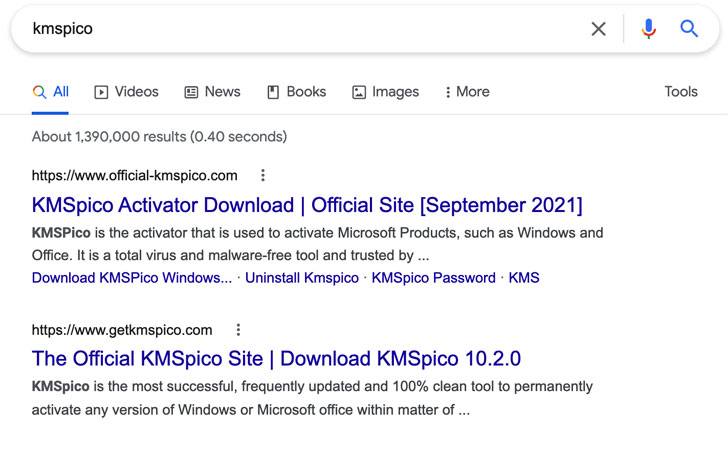
The malware, dubbed “CryptBot,” is an information stealer capable of obtaining credentials for browsers, cryptocurrency wallets, browser cookies, credit cards, and capturing screenshots from the infected systems. Deployed via cracked software, the latest attack involves the malware masquerading as KMSPico.
KMSPico is an unofficial tool that’s used to illicitly activate the full features of pirated copies of software such as Microsoft Windows and Office suite without actually owning a license key.
“The user becomes infected by clicking one of the malicious links and downloading either KMSPico, Cryptbot, or another malware without KMSPico,” Red Canary researcher Tony Lambert said in a report published last week. “The adversaries install KMSPico also, because that is what the victim expects to happen, while simultaneously deploying Cryptbot behind the scenes.”
The American cybersecurity firm said it also observed several IT departments using the illegitimate software instead of valid Microsoft licenses to activate systems, adding the altered KMSpico installers are distributed via a number of websites that claim to be offering the “official” version of the activator.
This is far from the first time cracked software has emerged as a conduit for deploying malware. In June 2021, Czech cybersecurity software company Avast disclosed a campaign dubbed “Crackonosh” that involved distributing illegal copies of popular software to break into and abuse the compromised machines to mine cryptocurrency, netting the attacker over $2 million in profits.
Source: https://thehackernews.com